Secret Validity Checks Launch in GitHub Advanced Security for Azure DevOps
Michael Omokoh introduces the secret validity checks feature in GitHub Advanced Security for Azure DevOps, showing how developers and security teams can now prioritize remediation of live secrets and stay ahead of credential exposures.
Secret Validity Checks Launch in GitHub Advanced Security for Azure DevOps
If you’ve ever felt overwhelmed by a flood of secret scanning alerts in your repositories, the new secret validity checks in GitHub Advanced Security for Azure DevOps are designed for you.
What Are Secret Validity Checks?
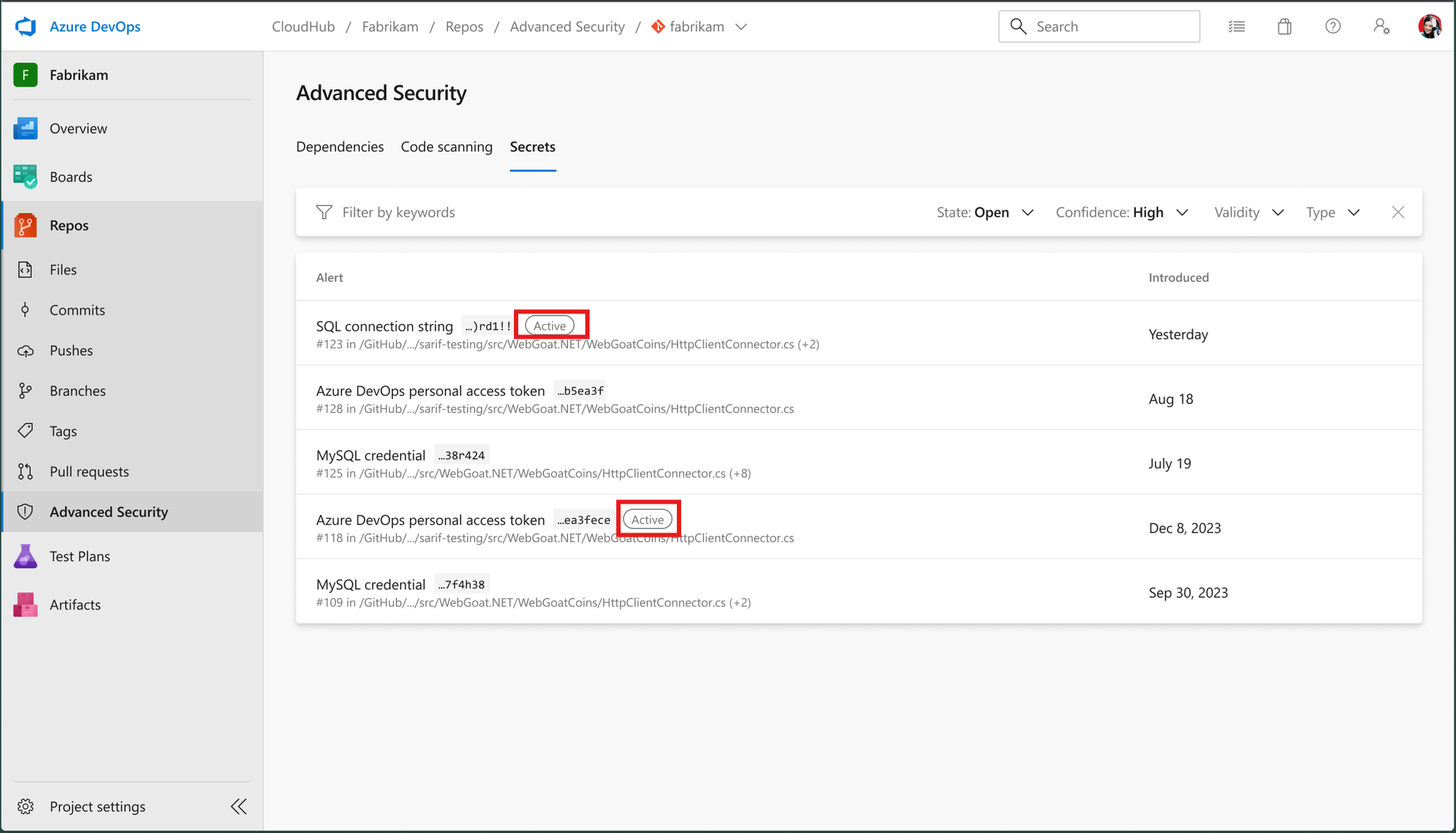
With this enhancement, each secret scanning alert is now labeled with a high-signal field: either Active (the credential is still usable) or Unknown (validity could not be determined). This lets you separate alerts that represent a real, live risk from those that do not—cutting down on wasted effort and letting you focus on what matters most.
How Does It Work?
- Secret scanning matches your code against known partner/provider patterns.
- For supported patterns, the platform automatically contacts the provider to check if the secret is still active.
- Alerts are labeled
ActiveorUnknowndepending on the result. - After you remediate a secret, you can run on-demand verification to check that it’s no longer usable.
For unsupported provider patterns, the status may stay ‘Unknown’—that’s normal. You can consult the list of supported providers for more information.
Typical Remediation Workflow
- Filter for Active secrets to focus on the most urgent risks.
- Review alert details, including the last time the secret was verified as active.
- Remediate: rotate or revoke the secret, remove references in code, and follow recommended actions.
- Verify the secret on demand to confirm it’s been neutralized.
- Handle Unknown secrets prudently, applying remediation if the blast radius or sensitivity is significant.
- Close resolved alerts according to your team’s policy.
Dealing With ‘Unknown’ Secrets
Treat ‘Unknown’ as potentially risky unless you have other mitigating information:
- Consider the blast radius (prod infrastructure vs. sandbox).
- Evaluate data sensitivity.
- Judge rotation cost—if it’s low, rotate anyway.
If in doubt, act as if the secret is still active.
FAQ Highlights
- Does this feature revoke secrets automatically? No. Validity checks only inform your prioritization—remediation actions remain manual (or automated by your workflows).
- Will all secret types support validation? Support will expand; check the provider patterns list for updates.
Getting Started
- Ensure that GitHub Advanced Security for Azure DevOps or the standalone Secret Protection experience is enabled for your repos.
- Make sure secret scanning is turned on—validity checks build on this foundation.
- No extra configuration is needed; validity checks start automatically for new, supported secrets.
Reference Links
- Explore secret scanning in greater depth
- Configure GitHub Advanced Security for Azure DevOps features
- Release notes for GitHub Advanced Security for Azure DevOps
By integrating these new validity checks, teams can reduce time spent on false alarms and focus remediation where it matters—making for a stronger, more efficient security posture.
Happy hunting.
This post appeared first on “Microsoft DevBlog”. Read the entire article here