Automate Open-Source Dependency Scanning in Azure DevOps with Advanced Security
Laura Jiang explores automating open-source dependency scanning in Azure DevOps with GitHub Advanced Security, focusing on setup, integration, and how results are surfaced for developers.
Automate Open-Source Dependency Scanning in Azure DevOps with Advanced Security
Author: Laura Jiang
Managing security across multiple repositories and teams can be a challenge, especially when additional setup is needed for each experience. In GitHub Advanced Security for Azure DevOps, there’s ongoing work to simplify feature enablement and make it easier to scale advanced security measures across entire enterprises.
Automatic Injection of Dependency Scanning Tasks
A recent update makes it possible to automatically inject a dependency scanning task into any pipeline run targeting your default branch. This ensures that both your production code and any code merged into your production branch undergo evaluation for open-source dependency vulnerabilities, enhancing overall security.
Enabling One-Click Dependency Scanning for Your Repository
To configure this feature, users need the “Advanced Security: manage settings” permission. Here are the steps:
- Navigate to Repository Settings:
- Go to Project settings > Repositories > Select your repository.
- Setting up for Standalone Products:
- Enable Code Security.
- In Options, confirm the selection of Dependency alerts default setup.
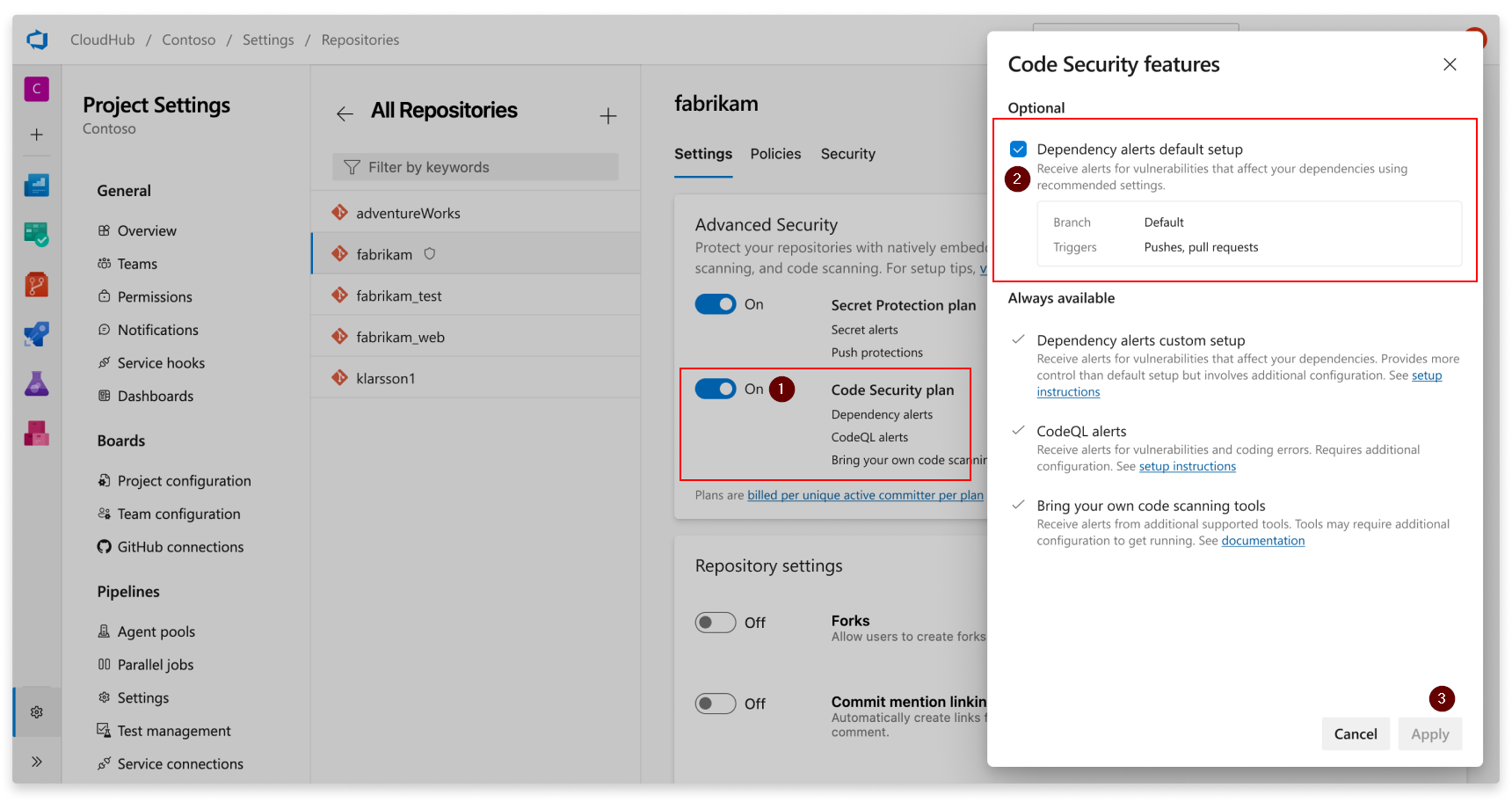
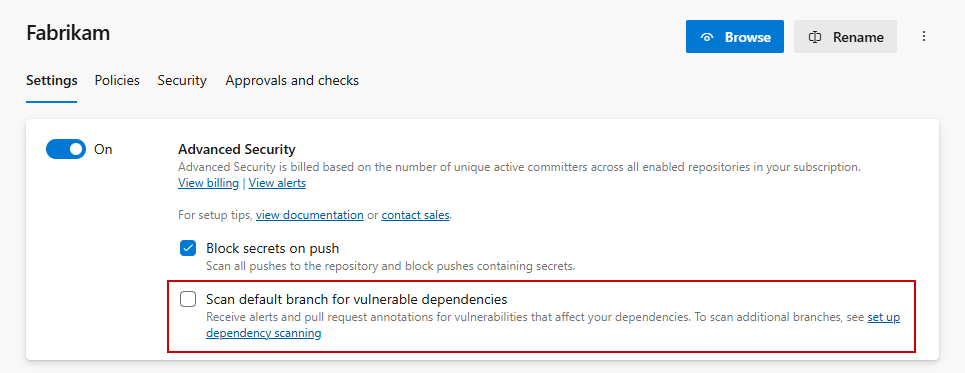
- Bundled Advanced Security:
- Use the checkbox to enable Scan default branch for vulnerable dependencies.
How Dependency Scanning Works
- On your next pipeline run targeting the default branch, the Advanced Security dependency scanning task is automatically appended near the pipeline’s end. Scanning typically completes within a few minutes.
- For teams without consistent CI/CD activity, scheduled pipeline runs are recommended to maintain consistent scanning coverage.
Flexible Exclusions
- If dependency scanning is already part of your pipeline or you have set the variable
DependencyScanning.Skip: true, the automated task will be skipped. This is useful for pipelines that shouldn’t be included in the scanning surface area. - To skip automated scanning on specific pipeline jobs, set the pipeline variable
dependencyScanningInjectionEnabledtofalse.
Reviewing and Acting on Scan Results
-
Upon completion, scan results are uploaded to Advanced Security and made available under Repos > Advanced Security.
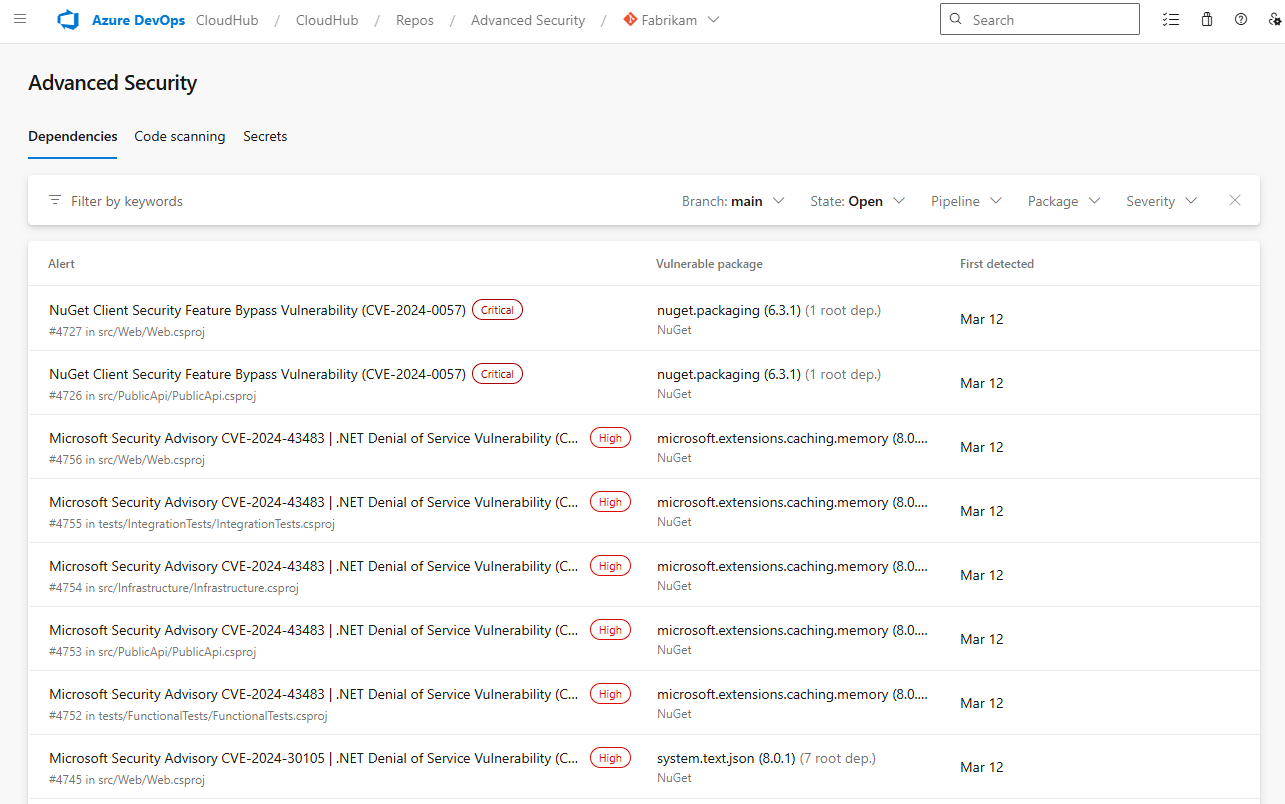
-
You can configure pull request annotations for dependency scanning, provided a build validation policy is set up. This injects scanning into all PRs targeting your default branch.
- Annotations for new findings are surfaced directly in the pull request (after scanning the default branch at least once).
- Existing issues shared between branches display in the Advanced Security tab.
Next Steps and Further Learning
- Teams are encouraged to try this feature and provide feedback directly or via Developer Community.
- Additional information can be found:
This post originally appeared on the Azure DevOps Blog.
This post appeared first on “Microsoft DevBlog”. Read the entire article here